Managing multiple AWS accounts can be a challenge for government agencies. This is because of the need to comply with different regulations and also the need to meet security requirements.
If you have a strategy for managing multiple AWS accounts. AWS Organizations lets you take control of your AWS environment and it is also a crucial element of organizations to manage their AWS resources under one Management account, which helps them meet compliance and security standards. It also helps them simplify management and billing of their resources.
There are multiple AWS services that you can enable at your organization, two of which being Amazon Guard Duty and AWS Security Hub. This blog will discuss how they work, what they do, and why you might want to use them. These are important components that helps creating a secure foundation for the AWS Organization.
How to setup Amazon GuardDuty for centralized threat detection
Amazon GuardDuty is a security service that continuously monitors for malicious or unauthorized behavior to help protect your AWS accounts and workloads.
The service continuously analyzes data streams from your AWS resources to identify potential threats.
GuardDuty is designed to detect threats by analyzing the following:
- Logs generated by Amazon CloudWatch, Amazon Elastic Compute Cloud (Amazon EC2) and Amazon Redshift.
- Activity logs from your AWS account, including API calls made using the AWS SDK or CLI.
- Security alerts generated by Amazon S3, Amazon EC2 and Amazon VPC Flow Logs.
Guard duty can be integrated with AWS Organizations, which allows you to set an AWS Account as Delegated Administrator. All Guard Duty findings are sent to this account so that the entire organization can be managed/viewed/analyzed from a single AWS account. Let's explore how to integrate Guard Duty with AWS Organizations, following these steps.
- Choose an AWS account that will serve as the Guard Duty Delegated Administrator and copy its account ID.
- Login to the Management Account and launch the Guard Duty dashboard, click Get Started.
- Scroll down to Delegated Administrator section, enter the appropriate Delegated administrator account ID, and click Delegate.
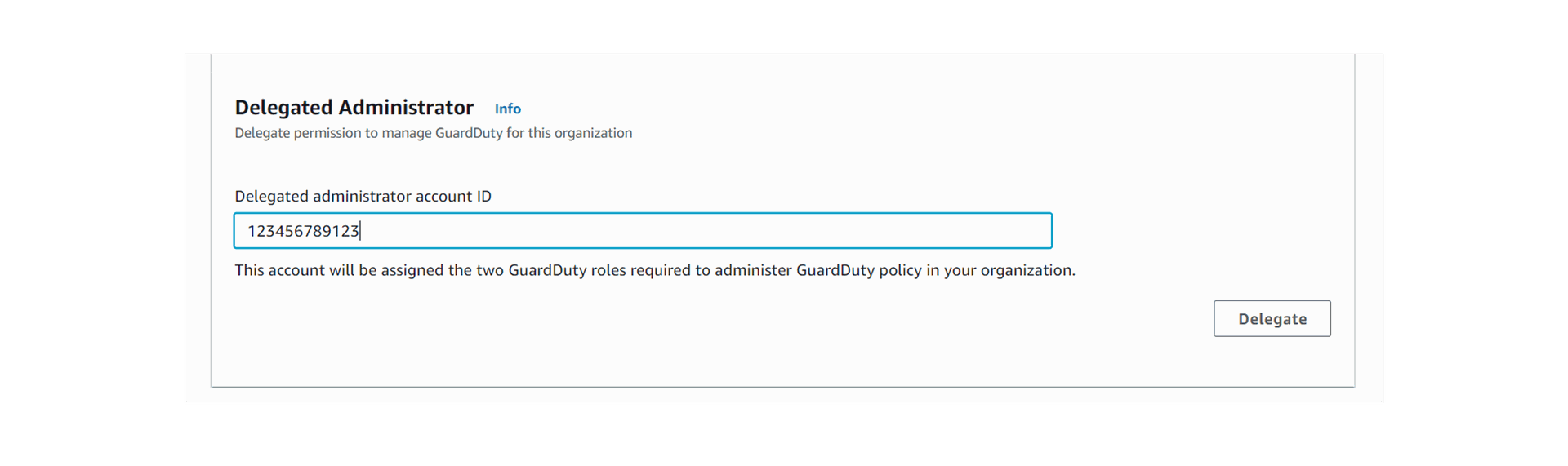
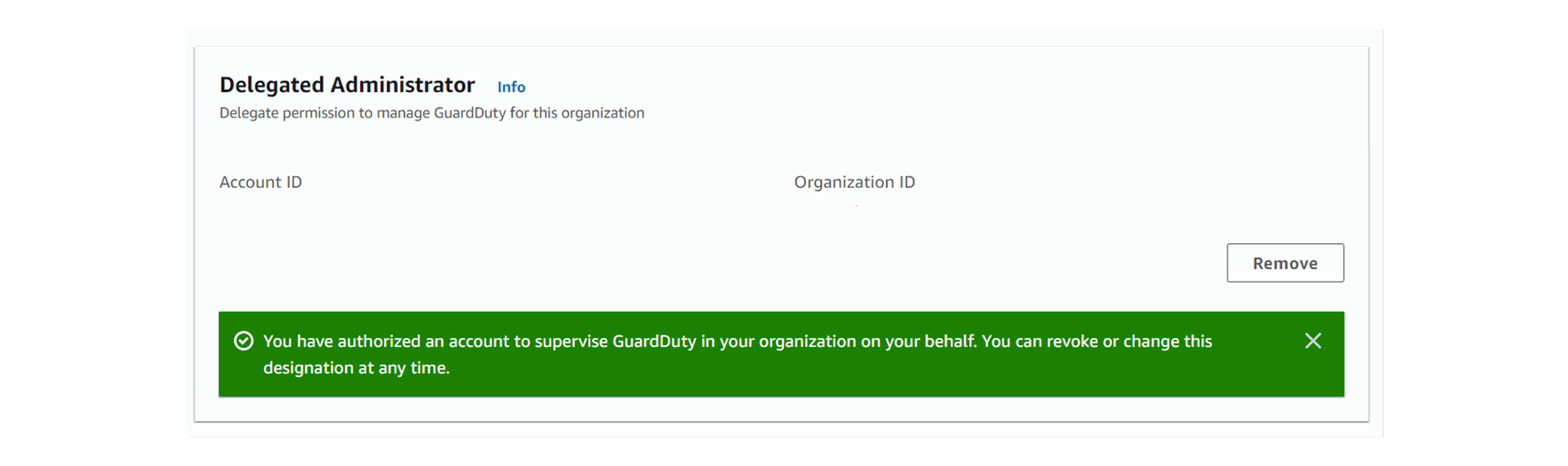
4. The Delegated Administrator account has been successfully configured as shown below:
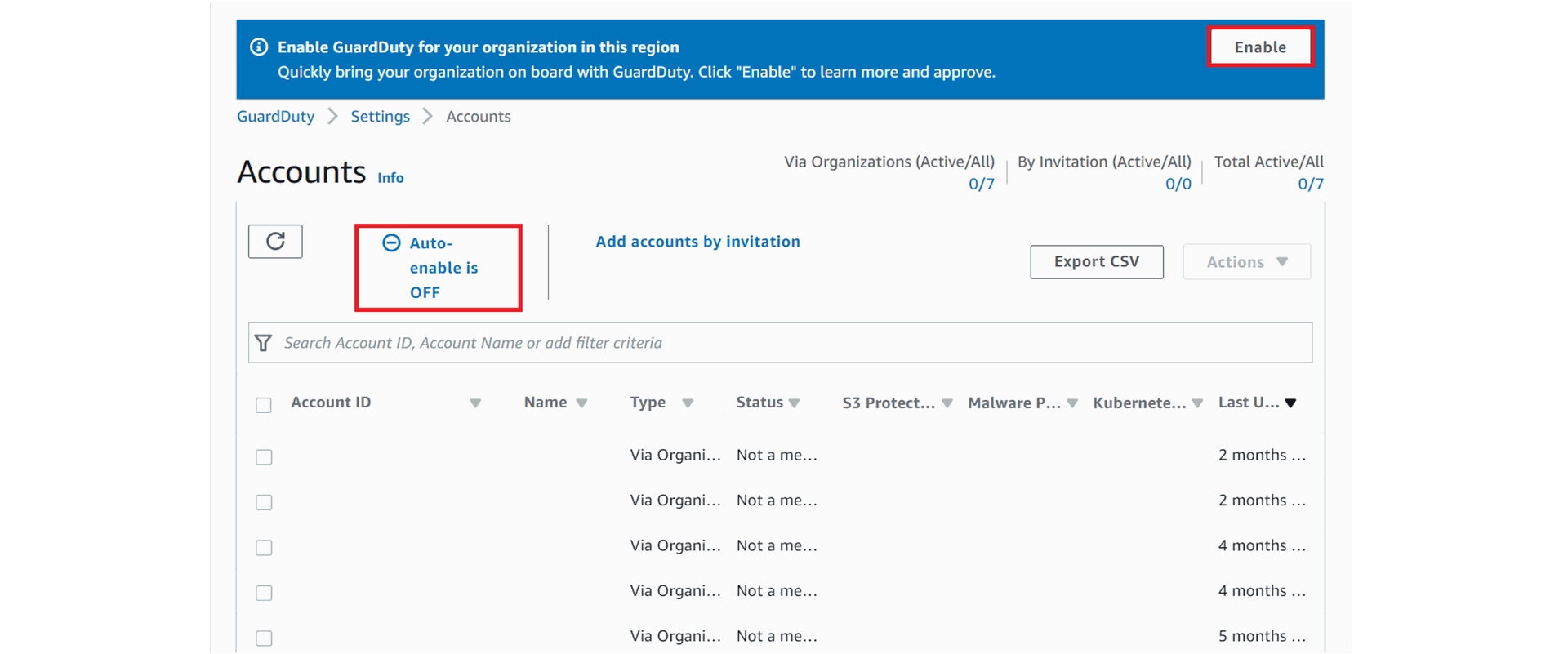
5. When you launch Guard Duty, you will likely see a blue information message box prompting you to enable Guard Duty for your organization, it is recommended that you enable Guard Duty in all supported regions, not just those in which you have deployed services or resources. When you add new accounts to your Organization, they will automatically be enabled with Guard Duty for the regions in which Auto-Enable was enabled.
6. By using CloudWatch Events and Guard Duty, you can set up automatic notifications by forwarding Guard Duty findings to a messaging hub. This will help increase visibility of your findings without the need for any intervention.
How to benefit from AWS Security Hub in AWS organizations
AWS Security Hub provides you with a comprehensive view of your security state in AWS and helps you check your environment against security industry standards and best practices.
Security Hub collects security data from across your AWS accounts, the AWS services you use, and supported third-party partner products. It helps you to analyze your security trends and identify the highest priority security issues.
With the ability to integrate with AWS Organizations, you can automatically enable Security Hub and its security checks in any existing and newly created accounts in the organization. By means of a Delegated Administrator account, you can also centrally view the security findings across an entire organization. Following are the steps to integrate Security Hub with AWS Organizations:
1. Choose the AWS Account that will serve as the Security Hub Delegated Administrator and copy its account ID.
2. Login to the Management Account and launch the Security Hub dashboard, click Go to Security Hub.
3. Scroll down to Delegated Administrator section, enter the appropriate Delegated administrator account ID, and click Delegate.
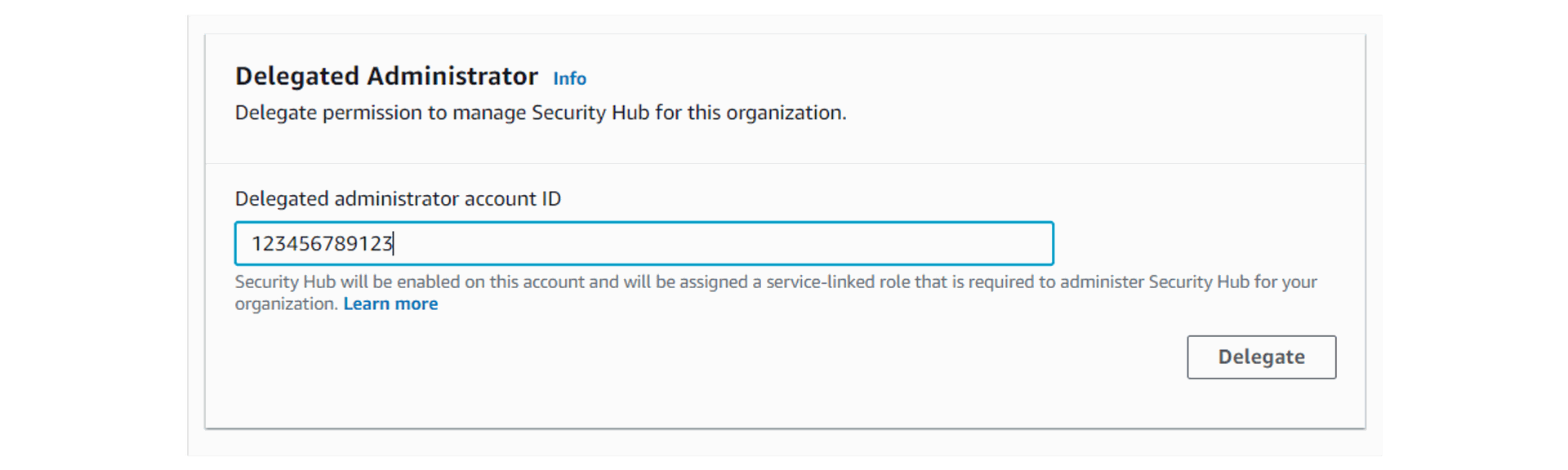
4. Launch the Security Hub service dashboard. On the Settings page, you’ll see 2 prompts. The first is a reminder to first enable AWS Config prior to auto-enabling Security Hub.
To auto-enable Security Hub for new accounts (in the specific region you are connected to), click Enable.
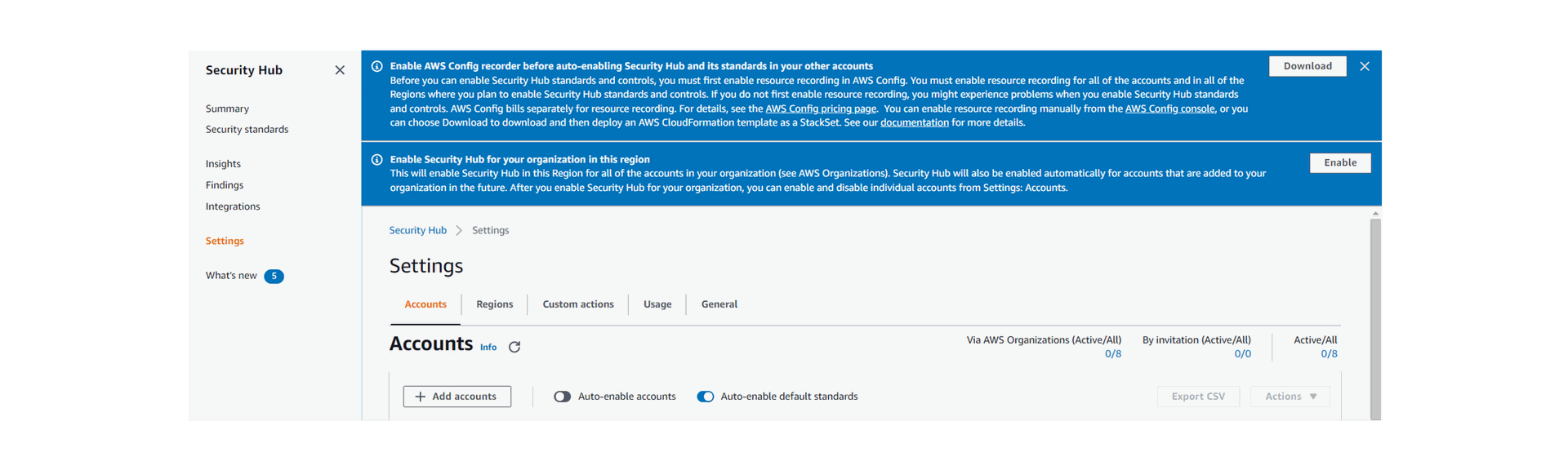
5. As shown below, Security Hub is now enabled for the Organizations member accounts and Auto-enable is also ON.
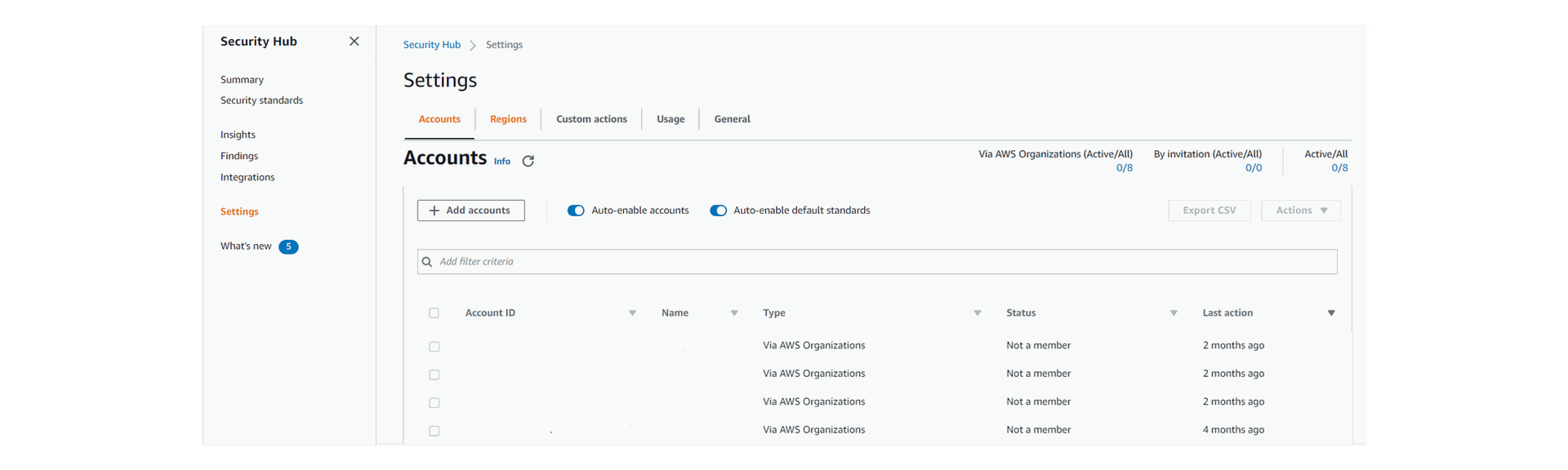
6. Now, you can go to “Summary” and view the findings and the insights.
Conclusion
Strengthen cloud security defense system for Government and critical businesses is crucial element when using AWS services in AWS organization account
As seen, Guard Duty and Security Hub both integrate easily with AWS Organizations, which help customers use AWS to build their security system. At the same time, they have also been an integral part of business-critical duties by governments and important organizations.
Learn more and gain use of cirrusgo's expertise
Book your FREE consultation now!



















